A Guide to Computers in Security

Computers are embedded in many security devices used in IP Camera Systems and Door Access Control. They have become essential in improving our safety.
Specialized computers and dedicated software control and enhance the functions of IP Cameras and Door Access Control Systems. This article describes how computers and software are used in these systems.
Overview of a Computer
A computer is an electronic device that processes data and performs tasks based on user commands. Computers are everywhere. These sneaky little critters are on our desks, phones, cash registers, refrigerators, stoves, and security devices.
A computer consists of the Hardware and Software:
Computer Hardware
The physical parts of a general-purpose computer are the monitor, keyboard, mouse, and central processing unit (CPU). A special-purpose computer without a display or keyboard is found in security devices. Physicist John von Neumann defined the basic architecture of a computer in 1945. It is incredible to realize that this basic structure still defines the architecture of today’s computers.
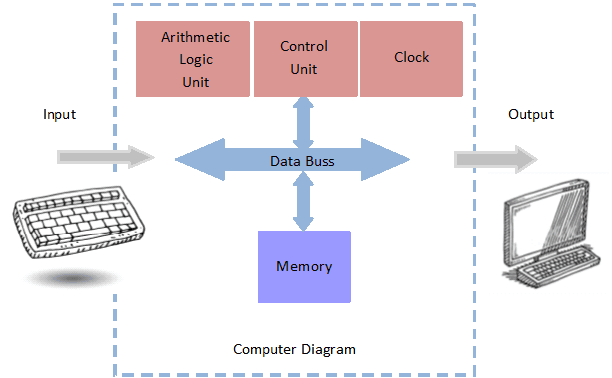
General-Purpose Computers
A general-purpose computer can be used for many different purposes. Your PC, Mac, iPhone, or tablet can be used to write letters, read emails, do computations, or explore the Internet. They are examples of computers that run many applications.
Dedicated Computers
A dedicated computer is designed to perform specific tasks. Examples include the computers in IP cameras, door readers and controllers, refrigerators, cars, and medical devices. These computers use specialized hardware and have dedicated programs (sometimes called firmware).
Computer Software
Software is a collection of programs that allow us to use the computer. Computer software runs on smartphones, desktops, security devices, and laptops. Regardless of their form, all computers have similar software functionalities.
A program is an application that performs a specific function, such as writing a document (Word) or calculating some math (Excel). Programs include the operating system (OS) and apps like web browsers, word processors, and games. Security equipment such as IP cameras has special-purpose programs. For example, the computer system in an IP camera processes the video, connects to the network, and connects to the Video Management Software (VMS). The latest AI-enhanced IP Cameras have advanced software that provides increased security.
The Operating System
The operating system (OS) manages the computer’s hardware and software resources, enabling you to run applications, access files, and connect to the internet. When you turn on your computer, the operating system is the first thing that loads, and it provides the graphical interface (the screen with icons, folders, and menus) that allows you to interact with the system.

There are several types of operating systems, with the most common being:
- Windows: Used in most desktop and laptop computers.
- macOS: The operating system for Apple computers.
- iOS (Apple mobile devices): is the OS for iPhones and Apple tablets
- Android (Google devices): OS for smartphones and tablets.
- Linux: An open-source OS often used by programmers and developers.
- Specialized Operating Systems that are specific to a device. Many specialized applications use portions of Linux or have developed their own custom OS. Axis OS and Hanwha Wisenet are examples of dedicated camera operating systems.
An App is a Program that Does Stuff
When the programmer finishes coding the program, we get an application (or App) that allows us to use the computer or smartphone to browse the web, write documents, play music, or manage emails. Security devices such as IP cameras use apps associated with software that runs on a computer or the cloud.
Programs like Video Management Software (VMS) and Access Control Management run on your desktop. Mobile Apps run on your smartphone to allow remote control and management of the central software and security devices.
IP Camera and Door Access Systems Use Apps
Many Video Management Software (VMS) and Access Control Management solutions use Apps that run on your mobile device and allow you to connect to the software running on a PC. For example, the Apps used with IP Camera Systems will enable you to see the video from all your cameras. The Apps used by Access Control Systems allow you to manage the system and remotely open a door.
Where Do We Get Applications
Some computer devices come with applications (Apps) already installed. For example, the Apple Mac, iPhone, or iPad includes Mail, photos, a camera, a calendar, and the Safari Web Browser. Windows computers come with an Email program and Microsoft Edge Web Browser.

If you want to view the video from your security cameras on your smartphone, you must add an App (Application) to your device.
An application can be added by downloading the program from a website or visiting an online store. For example, you go to the Apple Store to add an App (application) to your iPhone. If you have an Android device, you can download it from the Google Play Store.
Once logged into the store, search for the specific application you want. For example, search for “WAVE mobile” to get the Wisenet VMS mobile app.
Why do we Use “Username” and “Password.”
The username and password are essential for keeping your information safe. They are used to log in to your computer, purchase items online, and add new software applications (Apps).
- Username: This identifies who is using the computer. It can be your actual name or a unique identifier.
- Password: This secret code ensures that only you can access your account. A strong password typically contains a combination of letters, numbers, and special characters.
It’s a good practice to keep your password secure and change it regularly for enhanced security.
How to get the App
Getting the app from a website or app store can differ depending on where you get the application. In almost all cases, you will use your username, password, and credit card (if you purchase the app).
Here’s how to get an app on your iPhone:
- On your iPhone, open the App Store app. On your Android phone, go to Google Play
- You will need to Log into the store by using your username and password
- Tap the Search tab for a specific term, such as “Wave mobile” or “Wisenet Wave.”
- Click the Price or Get button.
- Double-click the side button on the right side of your iPhone—or the top button on your iPad— to complete your purchase. If you use Face ID or Touch ID to unlock your device, you’ll glance at your device or touch the Home button to authenticate the download. You might need to enter your Apple ID password to complete the download.
- Launch the App: After downloading, the app will appear on your home screen (iPhone/iPad) or in the Applications folder (Mac). Click the app icon to open and start using it.
Conclusion
Special hardware and software control the operation of security devices. By understanding the basics of a computer’s hardware and operating system and how to download apps, you can become a more confident and efficient user. Whether you download apps from the Apple Store or Google Play, your security devices can be reached from your mobile device.
If you would like help selecting your IP security systems, please call 800-431-1658 in the USA, 914-944-3425 everywhere else, or use our contact form.