Access Control Management Software Comparison
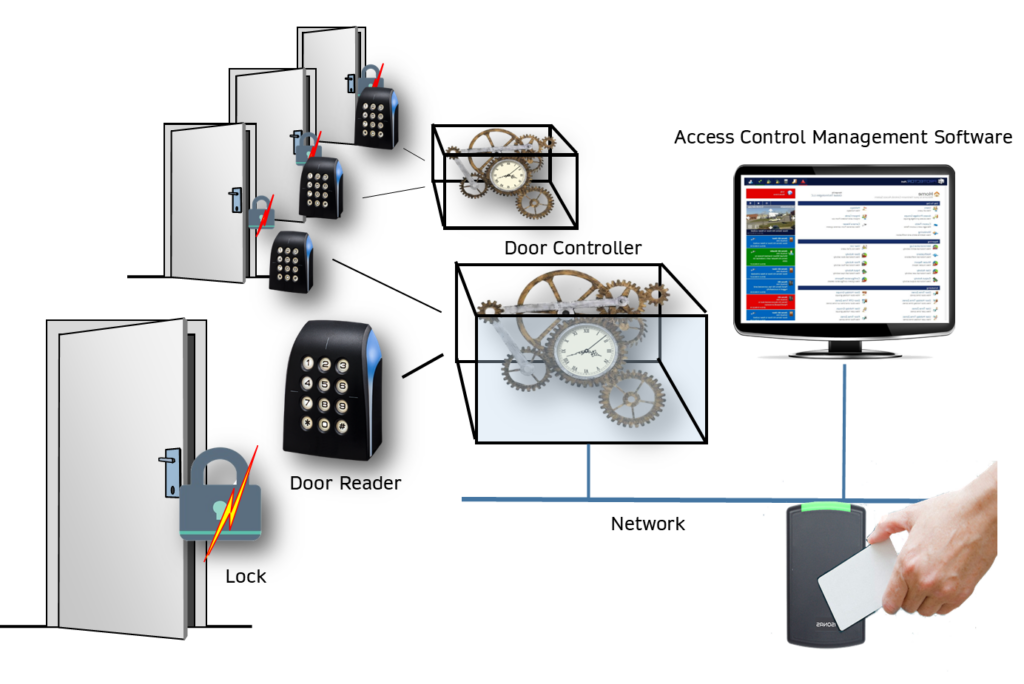
Are you planning to purchase a new access control system or upgrade an old one? The access control management software is critical because it provides many essential features and functions that will make a difference in the functionality of your access control system.
This article compares the features and functions of different access control management software.
Continue reading “Comparison of Access Control Software”