Installation Practices for Door Access Control Systems
There are several things to consider when selecting and installing a door access control system.
These safer practices increase the overall security of the system.
System security starts with the correct type of door-reader and secure wiring. It requires the right electric lock and an exit methodology for maglocks. It is also essential to select the right management software and additional security and safety features.
Best Door Readers for Access Control
The access control system includes a door reader and the access controller. IP door access systems use reader-controllers that include both the door reader and the controller in one unit.
There are four types of door readers. All these readers are available as simple door-readers that connect to an access controller or intelligent reader-controllers that connect to the network.
- Readers with PIN codes
- Readers that use an RFID card credential
- Mobile card credential readers
- Biometric door readers
PIN code door readers are the least secure. Since everyone is given the same PIN, it can be easily stolen or given to another person. In some cases, an inspection of the reader can reveal the PIN code by dirt or other wear marketings.
RFID readers are the most popular. People are given a credential that could be a card or keyfob that they carry with them. Each credential has a unique number, which allows the security personnel to track who has entered the building. Unfortunately, these credentials can be forgotten, lost, or given to another person.
Mobile credentials use a person’s smartphone as the credential. This method reduces the credential cost and provides increased security because people usually don’t give their smartphone to someone else. There are specialized Bluetooth connected smartphone readers that provide several options for entry. For example, you can swipe your smartphone, use your hand to gain entry, or even tap you phone in your pocket. To learn more, please look at our Mobile Credential Readers.
Biometric door reader-controllers provide the highest security level because they use a person’s fingerprint or other biometric information to gain access. Some biometric sensors, such as fingerprints and face recognition systems, have had some reliability problems. Still, new face recognition systems are more reliable and can even identify a person wearing a protective mask.
To learn more, take a look at our article, Comparison of Security Provided by Door Access Systems.
Wiring the Door Reader-Controller to the Electric Lock
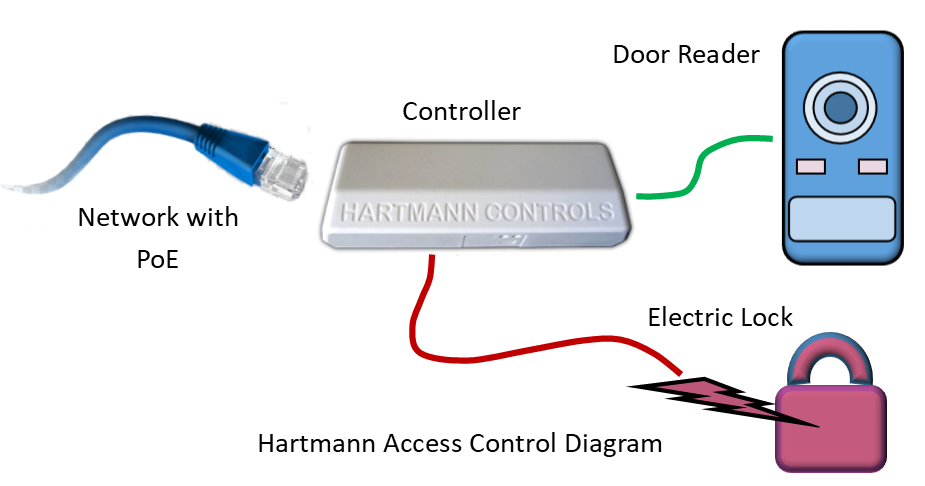
Simple door readers include a Wiegand interface that connects it to a controller, but the more intelligent reader-controller includes the relay to control the electric lock. When wiring the intelligent type reader-controller, it is essential to consider how a vandal may sabotage the wiring and gain entry.
If the reader-controller is mounted on an external door, the vandal may gain control of the relay wires. By breaking off the reader, and shorting the wires together, or opening the circuit, they may release the electric lock.
An internal relay controller should be used to prevent tampering with the external wiring. The external reader communicates with the internal relay control using a coded message (Wiegand or other protocol) that is not easy to duplicate. Even if the reader or reader-controller is broken off, the vandal can’t gain entry. For example, the controller at the door is mounted inside and provides vandal protection, and the External Door Kit (EDK) provided with the Isonas reader-controller also provides protection.
To learn more about how access control systems are wired, look at our article, IP Door Access Systems Wiring.
Selecting the Electric Lock

The electric lock is an essential part of your door access control system. You can select either a magnetic lock or electric strike to secure a door. The maglock is simpler to install but requires special exit hardware that is defined by local fire ordinances.
The electric strike is easy to install and are used to secure outer and inner doors but do not prevent egress from an area like the magnetic lock. It replaces the fixed strike place in a standard lock. It usually presents a ramped surface to the locking latch like a fixed strike, allowing the door to close and latch just like a fixed strike would. Many of the electric strikes require less than 400 mA of 12 VDC power, which means they can be powered using the same PoE that powers the reader-controller.
The door frame and current locking method can influence the type of electric strike. It is best to send a picture of the lock’s frame and door side so that the lock provider can suggest the correct electric strike.

Magnetic locks are used in certain situations where the strike can’t be used. They can be used in high-security areas where you need to track who enters and exits an area.
Since local codes determine the installation rules, maglocks should be used with care. The maglock mechanisms use an electromagnetic and armature plate to secure the door. Since the door is held shut by the maglock, it prevents easy egress. This means you will need to provide some way for people to unlock the door when they want to leave the area. Exit devices include crash bars, Request to Exit (REX) buttons, motion detectors, and connections to fire alarm systems. The local fire codes determine what type of exit devices are required, especially when there’s an emergency such as a fire.
Since the power supply holds the maglock shut, you may need to provide backup power if the power fails. It is essential to make sure that the battery power is wired so that all the exit devices operate correctly.
IP Door Access Control Management Software
Access control management software is associated with access control hardware. It determines who, when, and what door a person can enter. The software makes it easy to register the users and improves security by combining people into groups based on their entry requirements. For example, it may allow certain people to enter from 9 am to 10 am during the weekdays while granting management access anytime and any day. The software can also control who enters and where else they may have permission to enter the organization. For example, everyone can enter the front door, but only the IT staff can enter the server room.
Advanced Access Control Management: Some management software provides advanced functions that allow you to integrate with your IP Camera System, control the elevators, or configure the access control system from your mobile device. Learn more…
The access control management software is an essential part of the definition process when deciding the best access control system.
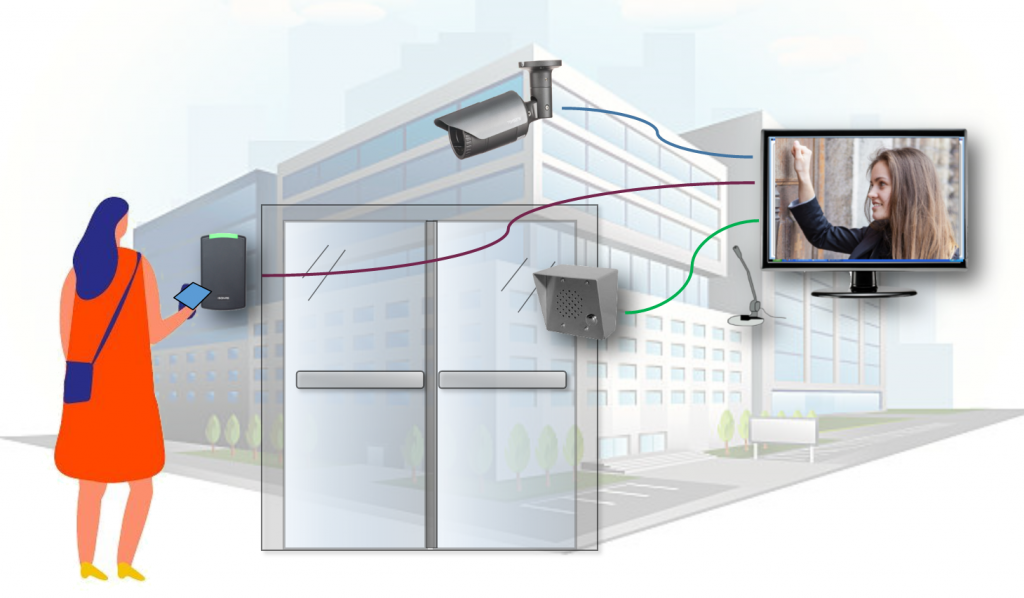
Adding Additional Security
Access control systems can be enhanced by adding temperature scanning and mask detection. The biometric temperature scanning panels can be used by themselves or added to existing access control systems. Intercoms and IP cameras can also be added to increase security. The intercom allows you to control visitors while the IP camera system can be used to view people at the door.
Access Control Best Practices Summary
There are several things to consider when installing an access control system. These include the door reader, the controller, the access control management software, and the wiring. IP cameras and intercoms can be added to increase the total security.
If you would like help selecting the right access control system, please contact us at 800-431-1658 in the USA, 914-944-3425, everywhere else, or use our contact form.