Remember when access control was limited to fitting a key into a lock and turning? You know the drill. You probably used one to lock your door this morning, and you’ll use it again when you go home this evening. Turn it one way you retract the deadbolt that holds the door closed and gains access. Turn it the other way, you fit it back into place, denying access to anyone without a key. Unfortunately, the lock and key system is an ancient innovation that is not up to the challenge of many of today’s security needs; this is where we need to upgrade to IP camera systems, electronic access cards, biometrics, and other modern technology.
The First Lock and Key
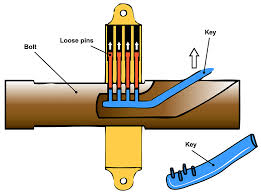
The first key unlocked the first lock close to 6,000 years ago in Egypt. The Egyptians used a very simple wooden locking mechanism composed of several small pins inserted into a wooden bolt close to its locking slot. When the pins were in place, gravity held them down, locking the bolt. When a small wooden toothbrush-type key was inserted, it reached the pins and raised them, unlocking the bolt.
Locks and keys have worked for us through the ages. They are easy to install, universally available, and offer simple secure access control. But they are hardly ideal. Who among us has not lost a key? Keys can break off in the lock if too much pressure is applied. Then you need a new key.
…and maybe a new lock.
And there’s no way to revoke a key’s “security clearance”. When a roommate moves out you can’t take her off an authorized list nor can a new homeowner or renter be certain they hold the only keys. In all these instances, security demands getting the lock changed. And with it comes a new set of keys.
Access Cards
Keys and keyholes may still be sufficient for residential use, but are all but obsolete at most workplaces, having been replaced by IP access cards and card readers. But cards, too, are going through a flux of change.
Barcode

A bar code is made up of a pattern of lines and spaces of varying widths and sequences. It may or may not contain alphanumeric characters. The information contained in this computer code is scanned into memory and resides on the card. When presented to a barcode reader at an entryway, it will unlock the door if the employee seeking access is authorized.
Bar codes were the first type of code to be used in access control. They are easy to create, simple to use, and cost little to produce. In fact, a user can print his own barcode using a PC-based application and apply them to blank cards and badges. This plus is also a minus. Since the barcode is there for all to see, anyone who sees it can reproduce, or counterfeit it. One way to get around this fault is to cover the barcode with an opaque film of some sort so that it must be read with a UV bar code reader but this adds to the cost.

Magnetic Stripe
When most people think of swiping a magnetic stripe, they think of their credit card. Swiping a magnetic access control card is no different The magnetic stripe, actually, a piece of coated magnetic recording tape holds information that identifies the holder as someone authorized to enter the facility just as a credit card holds account information.
Magnetic stripe access cards and badges are one of the most economic solutions since they are easy to produce. However, since swiping them puts them through the reader, they wear out and need periodic replacement. Add to this the fact that they are easy to forge and you can see why, although they are good for companies requiring only simple access control, they are not the answer for facilities with a need for tight security.
Proximity Cards
Proximity cards, like those used in IP access control systems, fill both voids left by magnetic stripe cards. Proximity cards contain a microchip embedded with encoded identity and authorization data, and an antenna to transmit it to the point of entry. When the employee approaches the door, he presents his proximity card, activating a so-called wake-up field that powers-up the electronics in the microchip so it can send the encoded identity data to the reader at the door.

Because the proximity card never comes into contact with the reader, it can last indefinitely. And the reader, since it can be hidden inside the structure, is resistant to vandalism and tampering, making proximity cards a secure, durable means of access control.
Biometric Cards
Keys, barcode badges, magnetic stripe and proximity cards all share a common security deficiency. They will permit access for whoever is presenting them whether that person is the rightful owner or someone who has stolen or found it. Biometric cards fill the gaping need for identity authentication.

The biometric card places the authenticating technology on the card. In many solutions, a fingerprint scanner resides on the card, enabling the card, itself to read the cardholder’s fingerprint in seconds. Users authenticate themselves right there on the card. If the fingerprint matches the encrypted fingerprint, the card system opens the lock, granting access.
Access control systems using biometric fingerprint and thumbprint authentication provide a higher level of security than systems that just verify a card anyone might be carrying. They do away with the possibility of a stolen or lost card being used for unauthorized access.
Biometrics in Development
At this time, the fingerprint is the most prevalent form of biometric authentication, but the technology is moving on, basing itself on a person’s unique features.
Facial recognition technology, currently used as a forensic tool promises to be the authenticated access control solution of the future. And beyond that, a futuristic-sounding biometric door access control system is in the works, one that does away with cards altogether. It bases access control on biometric recognition of the entry seeker’s mannerisms and gait as he approaches the door. If everything measures up the door unlocks.

Is it just me, or does anyone else wonder whether the day will be soon upon us when all we have to do is to request “Beam me up, Scotty.”?
While we await that day, if you’d like help in selecting the right IP door access control for your facility or information about IP surveillance camera systems, call 914-944-3425 to speak to a Kintronics sales engineer, or just fill out an information request form.