Selecting the right biometric reader
By Dennis Gallen
Biometrics is a much safer way to control door access than carrying a card or remembering a pin number. It’s more secure because you are identifying a person rather than something the person is carrying. The door credential can be stolen, but your face can’t.

What can biometric readers do? How do you select the right fingerprint reader, facial recognition system, or multimodal biometric system? By the way, the latest Biometric IP reader-controllers combine a number of physiological characteristics and are more flexible and reliable than the older units. There are a lot of different choices, but what is best, what provides the best reliability and repeatability? This article examines the technology and provides guidelines for selecting the right biometric system.
Unfortunately, sci-fi action movies and TV shows like NCIS have provided high expectations for biometric recognition; some of which are beyond the capability of current technology. For example, can these systems reconstruct a blurry face of a felon in a crowd of people at the airport? Not quite. At least not at a reasonable price. Facial recognition and other biometric systems can do quite a lot, but technology has some limitations. The good news is that today’s biometric technology, when used instead for basic door access, is surprisingly affordable and easy to learn and operate.
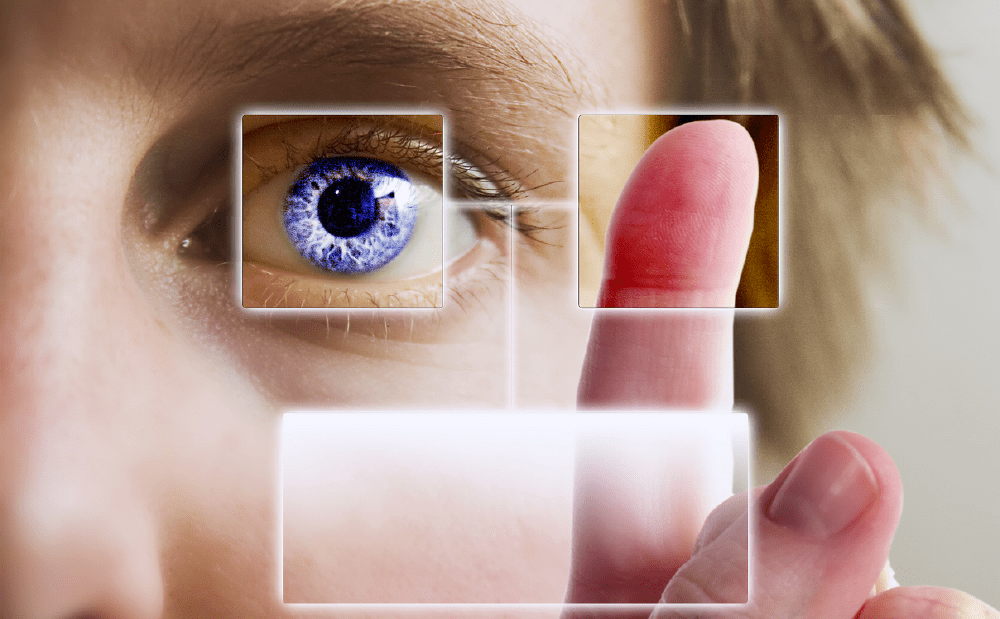
Biometric recognition is the automated method of identifying a person based on their physiological characteristics. Those physiological characteristics can include biometrics such as fingerprints, finger veins, palms, retinas, irises, faces, and voice.
Biometrics is better than RFID card credentials, but historically the cost has limited the growth of these systems.
New systems have recently been introduced that are less expensive and yet quite effective. They are also network-attached, making them very easy to install. The IP biometric reader integrates nicely with IP camera systems and is now part of the overall safety and security system.
In all cases, a person’s biometric attributes are registered and collected in a templet database so they can be used for comparison when the person tries to enter the door. The systems can be compared based on the speed of verification, and most importantly, their accuracy. Can the system repeatedly identify a registered person no matter what the conditions? We don’t want false rejections, and even more important, no false acceptance. Here’s a summary of the pros and cons of some of these systems.
Fingerprint Readers

The basics are simple. Each person’s fingerprint is unique, and the pattern created by the fingerprint has been quantified by law enforcement. It includes a number of basic patterns such as arch, loop, and whorl.
Some fingerprint systems capture the complete fingerprint while the new systems capture only key data points defined by the fingerprint pattern. The digital representation of the information contains far less detail, so it can’t be used to reconstruct the actual fingerprint image. This method requires less storage and is more secure.
There are many manufacturers of fingerprint readers, and they use different types of sensors such as optical, ultrasonic, and capacitance. Each of these methods claims to provide better performance, but the differences are not significant. They all work reasonably well when the fingerprint is well defined. There are some fingerprints, especially from people who have worn-out fingerprints, that are not easy to read. No matter what sensor is used, there is always a small group of people that have problems.
There is also a security problem with fingerprints. Devious minds have determined how to forge fingerprints using duplicating aids like latex, digital photography, and believe it or not – gummy bears. And social media being what it is, the information is readily available on the Internet.
Fingerprint readers are becoming more popular and provide secure door control access. The latest IP readers include more powerful microprocessors, increased storage, and better analytic algorithms. The new IP biometric readers attach to the network so they are very easy to install.
Finger Vein Readers
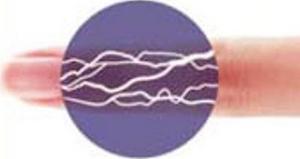
Finger vein readers are another method of providing unique identification. This technique captures an image of the vein patterns beneath the surface of the finger. In this case, the vascular pattern is detected using a near-infrared LED. The system detects the hemoglobin in the bloodstream, providing a distinct pattern.
This technique is much more reliable than the surface detected fingerprint readers. It is much harder to falsify because it only authenticates the finger of a living person. Finger vein readers are a more reliable system, but cost more than the standard fingerprint systems. The extra cost is worth the increased performance.
Facial Recognition Systems
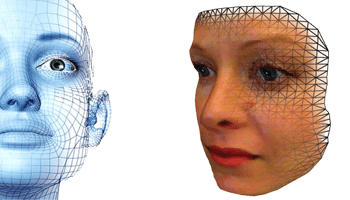
To identify a face, we need a certain amount of resolution across the face. Take a look at our previous article, “What IP Camera Resolution Do You Need?”. This means that a face must appear in a significant portion of the field of view. There are also other challenges such as the lighting, the head rotation to the camera, glasses, and other factors that change how the camera sees the face. Different algorithms are used to help maximize the effectiveness of these systems and the technology is continuing to improve.
Technology Used in Facial Recognition
The basic facial recognition system includes a good camera with a lens that provides the correct field of view for detecting all the features necessary and a computer software algorithm. Some systems use a separate camera and computer, while others are included in one unit. The latest facial recognition systems are self-contained units that attach directly to the network. These IP Facial readers are very easy to install.
There are two classes of systems, one that attempts to detect a person in a crowd, and another that provides door access control using a known and relatively small templet database. Just to give you some idea of the problem associated with recognizing a face in a crowd, some systems can match a face, but not if the person has a different expression on their face than the original stored image. So if you don’t want to be recognized in a crowd, just make a funny face. The systems that provide door access are less complicated, and cost less than systems that attempt to identify a face “in the wild”.
Facial recognition systems use various analytics, such as the shape of the face, the distance between eye pupils, skin texture, and 3D recognition. At least one system, FST, adds body shape and motion to the algorithm to improve accuracy. This system is more expensive but can actually confirm a person’s identity as they walk towards the door (camera). It can also detect if there are other people approaching the door and make a decision about whether to unlock the door or not.
Multi-mode Biometric Readers

What happens if a person is wearing a hat, or sunglasses and the facial recognition system doesn’t work? Or if someone has fingerprints that are hard to read? Well, now there is a solution. There are new multimodal biometric IP readers available that dramatically improve reliability and security. For example, there is the multi-mode reader that reads both fingerprints and vein patterns. If one doesn’t work the other will. If you would rather use a facial recognition system, there are IP readers that provide both facial recognition and fingerprint analytics. There are even readers that provide fingerprint, facial, RFID credentials, and even pin number access control (total 4 credentials) which can be mixed and matched when configuring door access permissions.
Multi-mode bionic systems also can provide a higher level of security. Suppose you would like to assure that the right person enters the building and then want to control access to certain secure areas in the building. You can use a multi-mode bionic reader at the front door, and then have less expensive RFID readers at the internal doors you want to control. You have now increased security throughout the building by assuring that the right person has entered, and then only used a credential for further access control. Of course, you can place bionic readers everywhere, but this is a strategy for saving some costs.
The latest multi-mode bionic readers provide much higher reliability than the single-mode readers, yet are in the same price range.
Summary
Biometric IP readers improve safety and security by controlling access of a person’s “identity” rather than the credential they carry, or what they know (i.e. PIN code). The new biometric readers attach to the network, are more powerful, yet easier to install than the older systems. Multimode biometric IP readers are more reliable and flexible because they measure a number of different biometrics. They offer users more choice when authenticating. Since pricing has decreased, more people have started to use these new IP door readers and the market has grown.
For help selecting the right door access control system, just contact us. We can be reached at 1-800-431-1658 in the USA, and at 914-944-3425 everywhere else, or just use our contact us using our form.