Description of the Components of the Access Control System

Door access control is part of an overall security system that keeps our organizations safer. The access control system ensures that only registered people can enter the organization. It provides four essential functions:
- It identifies who can enter
- Determines what door a person can use
- Defines when they can enter
- It maintains a record of everyone who is registered and keeps a list of who goes in and out
This article describes the components of an access control system.
Components of the Door Access Control System
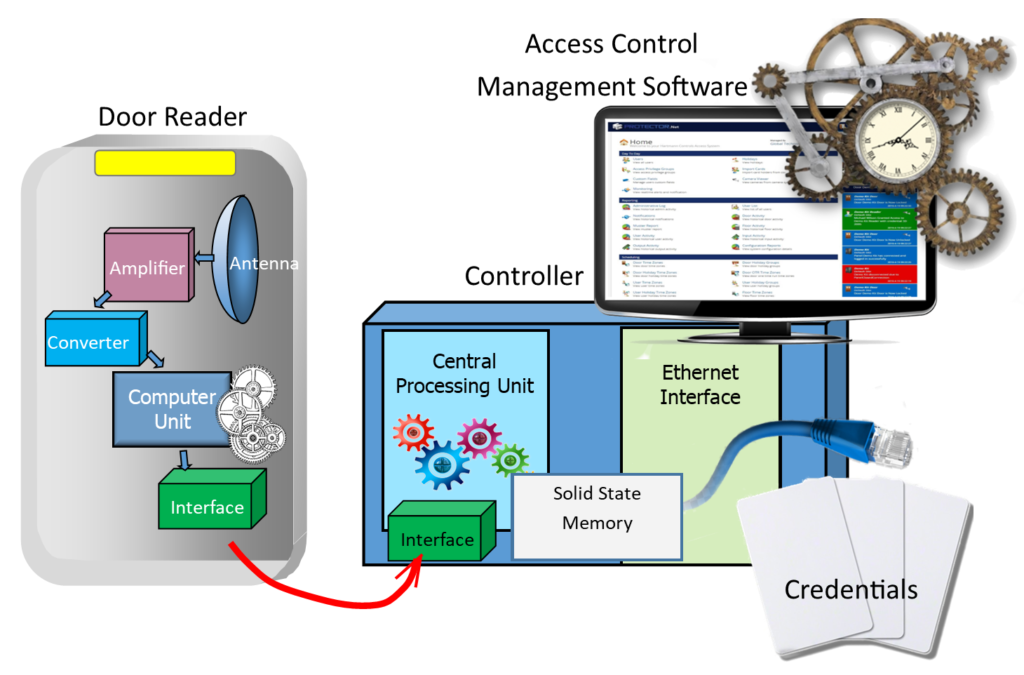
The access control system consists of four primary components
Door Readers read the credentials. The Controller compares the credential presented to the reader to the registered list. The Management Software provides registration functions and manages the list of users. And the Credentials are used to enter the door.
Door Readers

As the name implies, the door reader reads the credential provided by a person who wants to enter the door. The credential can be proximity or RFID card, smartphone, or biometric information. It is essential to select the right door reader for a specific type of credential. The readers connect to the Controller.
Proximity Door Readers
Proximity RFID readers connect to an access controller such as the Hartmann controller, using the Wiegand or OSPD (Open Supervised Device Protocol) interface. You can select readers for indoor or outdoor applications. Some readers include keypads that can be used instead of a credential or enhance security by requiring a secondary access code.
Smartphone Door Readers
This touchless door entry method saves money on card credentials. The app on your smartphone provides the ID to the door reader. The Isonas reader-controller can use blue-tooth connected mobile credentials. The Hartmann Enterprise Door Access Control System includes more sophisticated mobile readers that provide a variety of methods for opening the door. For example, you can wave your hand in front of the reader without taking out your phone.
Biometric Door Readers

Biometric door readers are usually combinations of a door reader and Controller. Biometric reader-controllers attach to the network and measure a person’s unique physiological characteristics.
Fingerprints, finger-vein, palm, retina, iris, face, and voice are examples of biometric identification. Biometrics provides far better security than RFID card credentials. It is better than cards or PINs because you are identifying a person rather than something the person is carrying. Many of the readers available Have multiple access keys. They can read biometrics as well as RFID cards and PINs. Please look at our article Comparison of Security Provided by Door Access Systems for more detail about the security levels provided by different door access control readers.
The article Door Readers for Everyone provides more details about different door readers available.
Access Controller
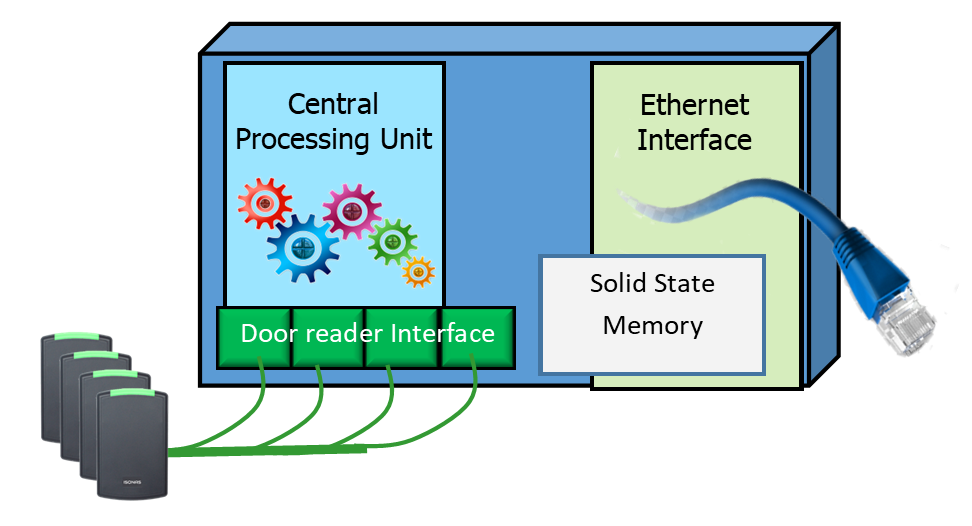
The Controller contains a small computer, memory, and network interface circuits. It maintains the list of all the people who can enter the organization. The ID in the credential is compared to the authorized list and used to determine if the person can enter. It also includes a user interface that provides the management of all the organization members.
Several door readers connect to the central Controller. The problem with this configuration is that it requires many wires connected to each door reader. The cables included the Wiegand interface to the reader, the door control wires such as the electric lock control, and the door sensor. It also required power for the lock to be wired to the door.
Today’s controllers are small, placed close to the readers, and easier to install. They connect to the network and are managed by access control software. The Enterprise Access Control System is an example of a system that uses small controllers located at the door.
Reader-Controller systems
The Isonas door system is an example of an access control system with an embedded controller. It is the easiest system to install because there are fewer wires required. The reader-controllers connect to the network and have a pigtail that controls the door lock. All the controls are at each door.
Door Access Control Management Software
Access control management software determines who can enter, what door they can use, and when they can come in. Each person is given a credential containing a unique ID number. The software is used to enter the credential ID of each authorized person.
Note that each access control system has its own Access Control Management Software. The software controls the specific kind of door readers and controllers, so they must be selected with the matching system.
For example, the Isonas cloud-based management software provides essential access control functions suitable for small to medium applications.
The Enterprise management software provides more capability, such as if-then logic functions, elevator control, and visitor management. It also integrates with many IP camera systems. Even though it is designed for large, sophisticated environments, it can also be used in small applications.
Access Control Credentials
There are several types of credentials used in door access control systems. Each credential provides a unique ID associated with the person registered in the access control system.
RFID Cards
The RFID or Radio Frequency ID card is the most popular type of credential.
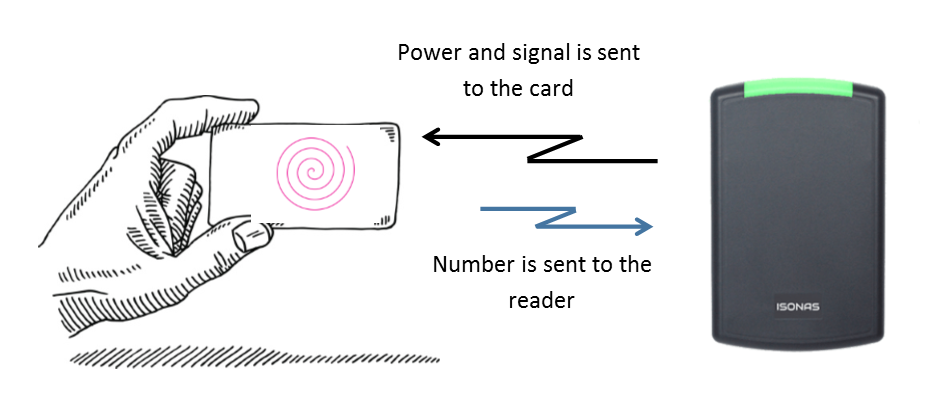
The credentials have embedded ID circuits and an antenna. The RFID door reader broadcasts a signal that is received by the credential’s antenna. The broadcasted radio signal contains enough power to energize the circuit in the credential. Once the electric circuit in the credential gets the power, it sends back a signal to the access control reader that includes its identification (ID) number.
Mobile Credential
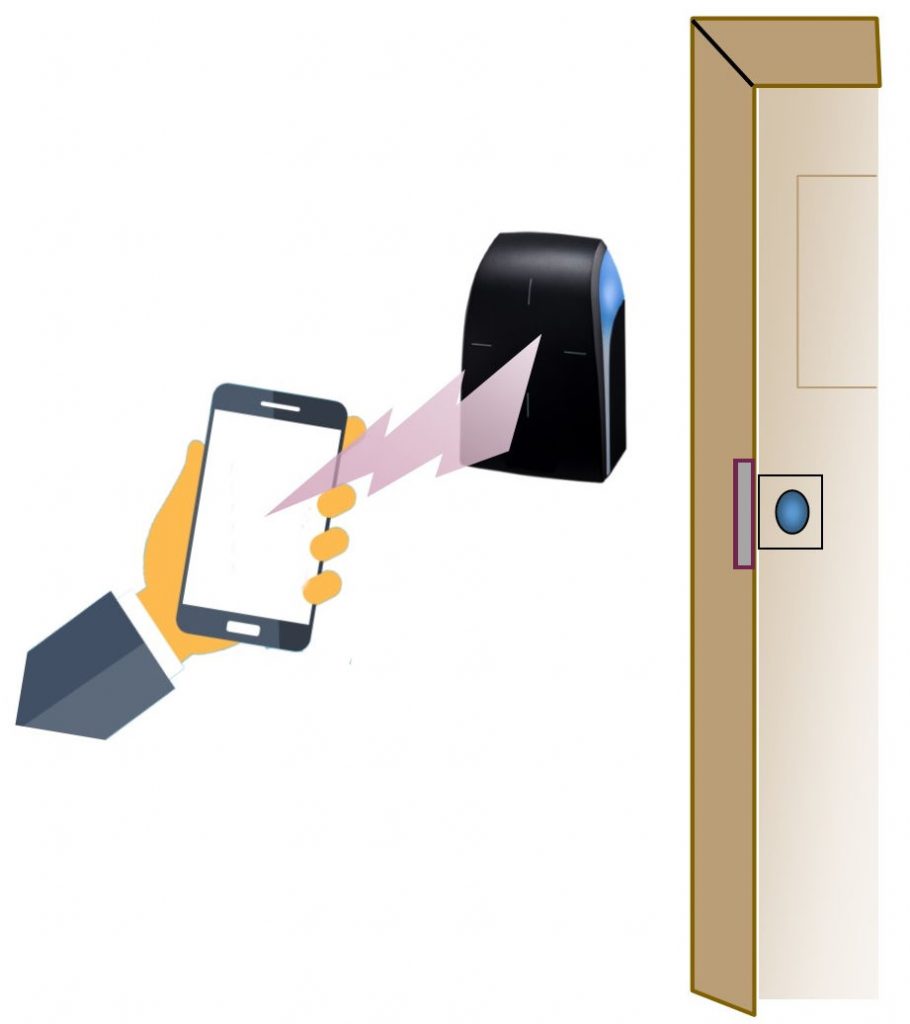
A mobile credential is an authorization ID like a Prox card or keyfob. The benefit is that you don’t have to purchase card credentials. The ID number is held in your smartphone app instead of a card. The smartphone can connect to a door reader using Bluetooth, NFC, or even WiFi. Bluetooth (BLE) is the most common communication used in the security market.
Mobile credentials are less likely to be forgotten at home. The smartphone is a personal device that has become a part of our regular daily activity. Because of its importance, it is unlikely to be given to another person. The added security of unlocking the smartphone adds additional security against misuse.
Biometric Credential
Biometric door readers are the most secure type of credential because they identify the person rather than what they carry.
Biometric readers can use fingerprints or have facial recognition systems. There are also palm readers and finger-vein systems. Each of these biometric readers provides a variable level of reliability. Fingerprint readers are the least expensive but sometimes have difficulty reading worn-out fingerprints. Facial recognition readers provide better reliability but can have problems if someone wears dark glasses, or something obscures the face. Finger-vein readers are the most reliable but cost more.
Summary of How Door Access Control Systems Work
The safety officer provides credentials to each person and logs them into the access control software system. Door access control determines who can enter a specific door at a particular time. It also maintains a record of who used the system. The system consists of door readers, a Controller, access control management software, and credentials.
To learn more about access control, please contact us at 800-431-1658 in the USA or 914-944-3425 everywhere else, or use our contact form.