Technical Advances in Access Control and IP Camera Systems Enhanced Security

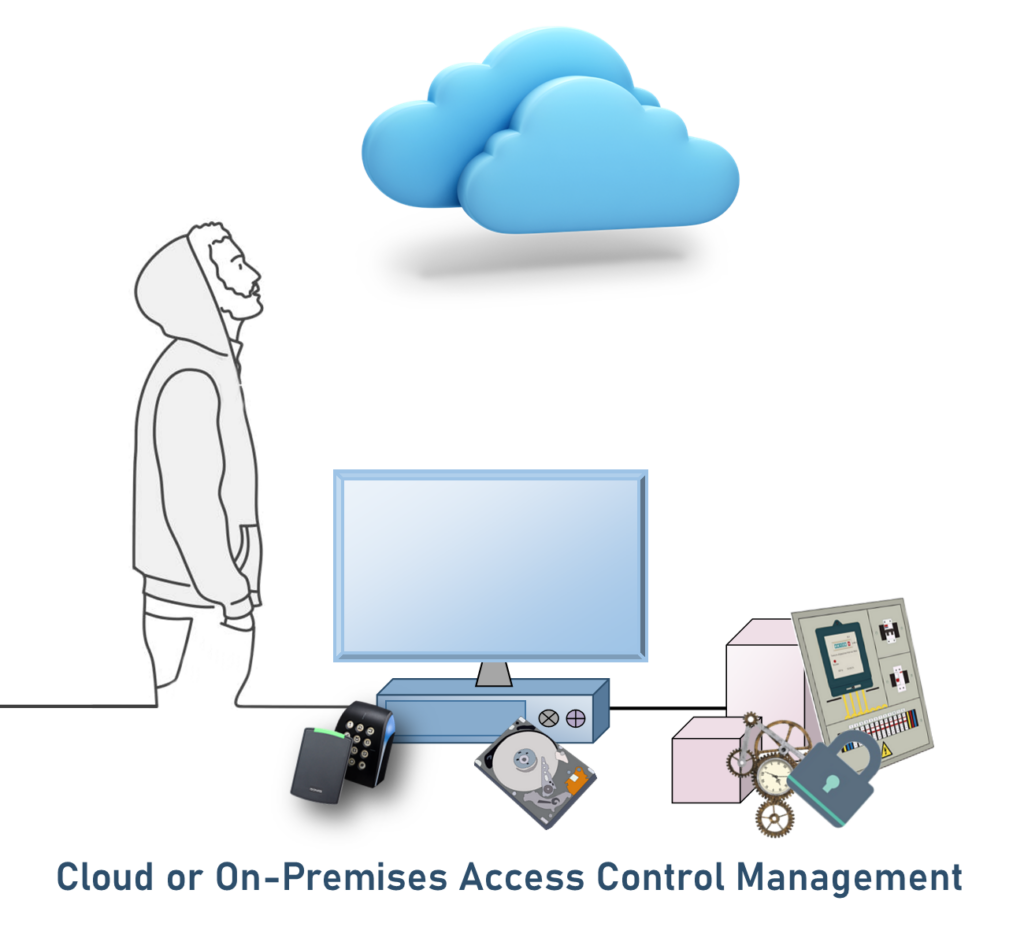
In 2023, several technological advancements significantly impacted surveillance cameras and access control. IP Camera Systems were enhanced by AI systems, and Access Control used more secure biometric and mobile credentials.
This article reviews some of the technical advances realized in 2023 that increased our security.
Continue reading “Tech Advances in IP Camera and Access Control Systems of 2023”