What You Can Do to Improve Security
With all the gun-related tragedies at schools and other facilities, what can we do to increase our security? Securing your facility, school, sporting events, or concerts have become more complicated.
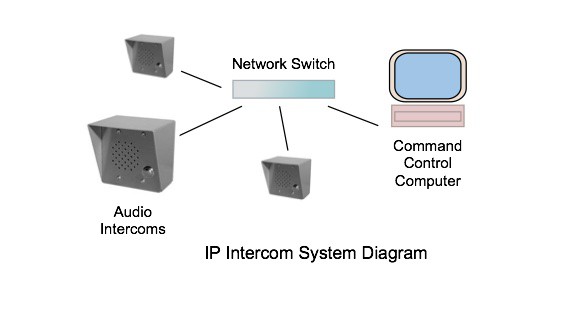
IP camera systems used to be enough to monitor the facility, but today we want to do a lot more. We want to prevent unauthorized access to our buildings, prevent people from bringing in weapons, and we want to provide campus-wide paging systems that keep everyone informed of any emergency.
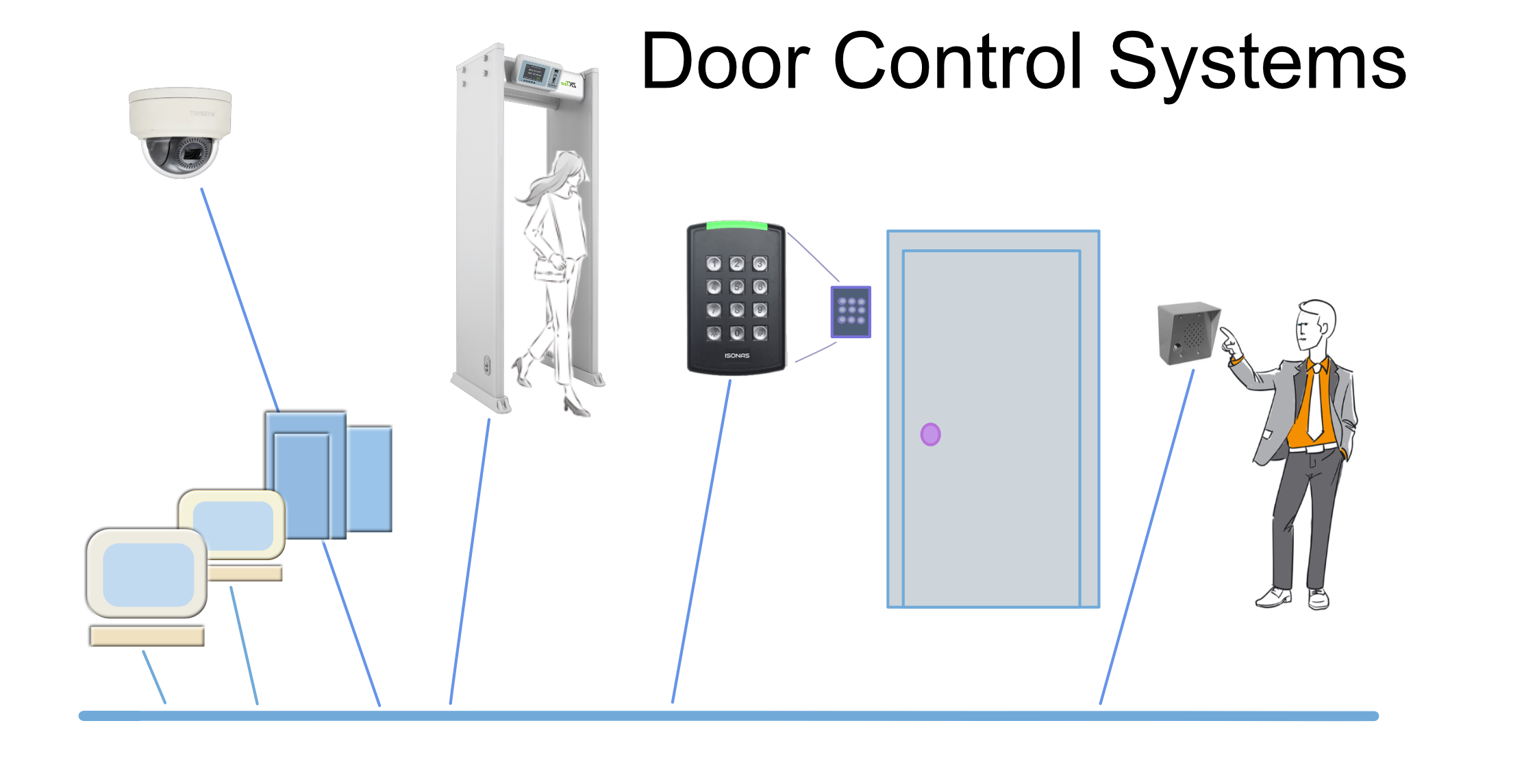
Access control systems include more than just a door reader. They can include intercoms, cameras and even walk-through metal detectors. Each of these security systems adds another level of safety. The different components play unique roles in your overall security. This article reviews the various parts and when to use them. It provides guidance about what technology to use and an overview of how they work.

Door Control Readers:
IP door readers control who can get into your facility. Access is controlled by credentials which can be a card or key fob. There are also biometric readers that can detect your face or fingerprint.
When to use IP Door Control Readers:
They are best used when you need to control entry to your building, department or individual room, and don’t have a guard.
How IP Door Readers Work:
The simplest readers use credentials that a person carries. More complex readers utilize biometric information. Credentials are available in different form factors. There are thin cards that can be placed in a person’s wallet, thick cards that usually have a hole that allows them to be worn on a lanyard, and key fobs that can be placed on a person’s keyring. Some new door readers can also use a person’s smartphone as the credential.
Biometric readers use a person’s fingerprint, face, or even finger-vein to identify a person. It is a much more secure way of controlling entry since you are verifying the person rather than the credential they are carrying. To learn more about the security provided by the different types of door readers, take a look at our article, Comparison of Security Provided by Door Access Systems.
Walk Through Metal Detectors
Metal detectors are used in schools, sporting events, government offices, and concerts. They are part of a total security system that includes cameras, door access control, and emergency paging systems.

When to Use Walk-through Metal Detectors
Metal detectors are used to prevent weapons from entering a facility. They can detect guns and knives and any other metal object that could be used as a weapon.
How Walk-Through Metal Detectors Work
The metal detector works by generating a short pulse induction magnetic field across the opening. If a metal object passes through the detector, it creates an echo pulse that can be detected by the electronic circuits. To learn more about how they work read our article, How Walk-Through Metal Detectors Work.We also have a video posted that provides the science behind this technology.
Intercoms at Doors
IP intercoms are placed near the door you want to control and allow a visitor to contact the security person. They interface with door readers or electric locks to allow a remote security person to open the door. They work with IP cameras systems to increase security.
When to use Intercoms
Intercoms are used to manually control entry of visitors. When they are used with cameras, they allow the security person to see and talk to the person at the door.
How IP Intercoms Work
The intercom is connected over the network to a computer. When a person pushes the call button on the intercom, an alert sound occurs. This notifies the person assigned to security that someone is at the door. They can then talk to the person and release the door lock (or not). If an IP camera is placed at the entrance, the security person can also see the person at the door. The camera provides additional security since it allows you to determine if the visitor is alone or not.
IP Camera Systems
IP Cameras placed at strategic points inside and outside the building help detect dangerous situations.

When to Use IP Cameras:
IP camera systems have primarily been used to record video of essential areas. They can be used to determine who stole the laptop, but historically have not been able to notify you when the actual theft occurs. The latest IP cameras provided immediate alarms. The built-in video analytics can detect problems and notify security as soon as they happen.
How Smart IP Cameras Work:
The latest IP cameras include analytics that creates an alarm if a person crosses a predetermined line. They can also detect if a person leaves an object or takes an object from a room. These automatic features dramatically increase security by providing alarms as soon as the danger is detected. Our video describes, How the IP Camera Works. You can learn more camera analytic features in our article, The Intelligent IP Camera.

IP Emergency Paging Systems
Network attached paging systems use the local area network to distribute sound. The small amplifiers have a network connection and can drive a few speakers. A page can be sent from a computer on the network or a VoIP phone.
Network attached paging systems use the local area network to distribute sound. The small amplifiers have a network connection and can drive a few speakers. A page can be sent from a computer on the network or a VoIP phone.
When to Use an IP Paging System
When you need a paging system that allows the security person to give instructions to many buildings on a campus, or to just page to a single building, to a floor or even a single area. The IP based paging system provides precise control of where the page will be heard. The same system can also be used as an intercom system. This allows the security person to have a conversation with people located in key locations.
How IP Paging Works
The network attached speakers include a built-in amplifier, micro-computer, D to A Converter, and a network connection. They also can include an optional microphone so you can use these speakers as intercoms. For more details about how they work take a look at our article, How IP Powered Speakers Work.
Summary
IP security technology can be used to increase our security. This includes IP camera systems, Intercoms, Walk-through metal detectors, door access control, and paging systems. To learn more about How Technology Can Help in Active Shooter Situations.
To learn more about the security systems available, please contact us at 1-800-431-1658 in the USA, or at 914-944-3425 everywhere else, or just use our contact form.