Automated Network Attached Paging Provides Emergency Announcements
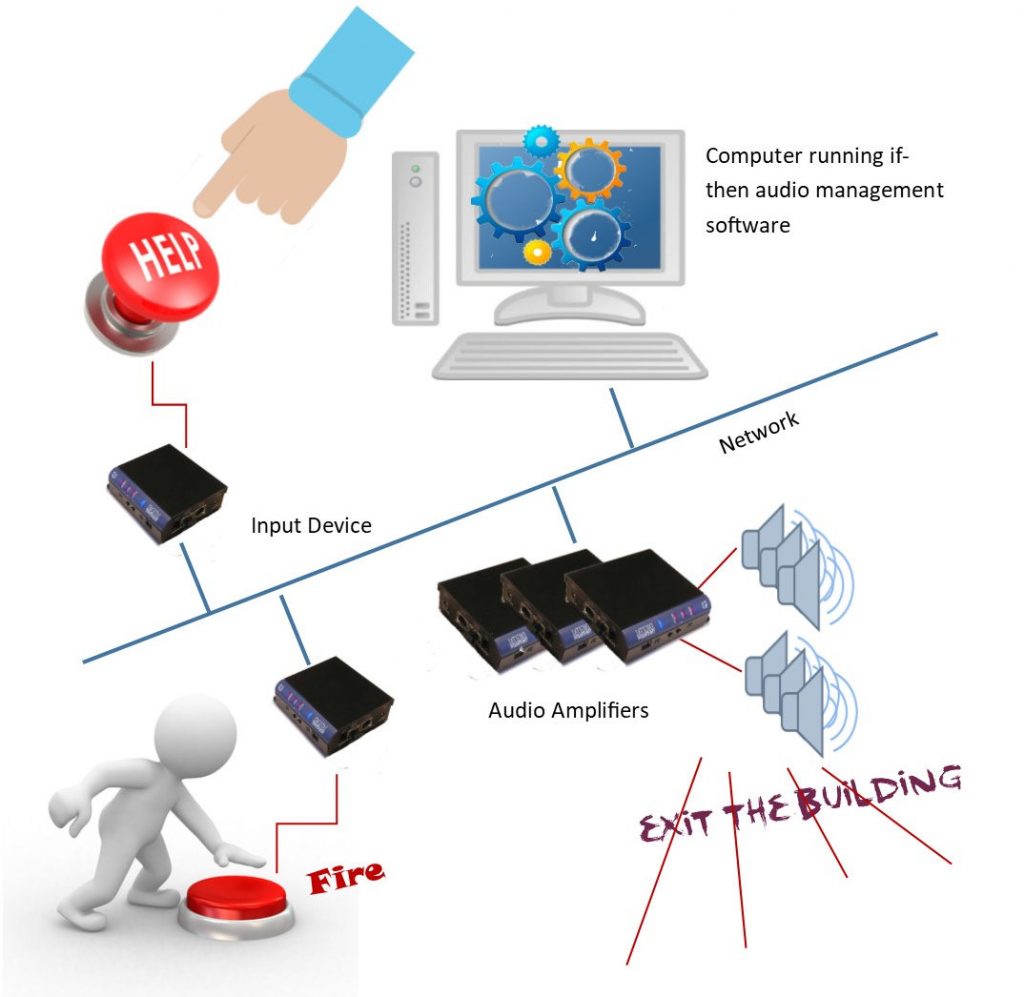
Network attached paging systems are replacing the older analog paging systems. They are not only easier to install; they provide increased functionality. One of the most helpful features of this system is its ability to make automated announcements. You can push a button and make a pre-recorded page, or automatically notify everyone about a weather emergency received from the national weather service. The automation feature can even convert text messages to audio announcements.
Digital Acoustics was the first company to provide IP paging systems. Their PA over IP product was introduced in 2004 and included small audio amplifiers that were attached to the network. Today there are a number of companies that provide IP type paging systems, but Digital Acoustics continues to provide the most flexible and economic systems. Here’s how to use automated Paging.